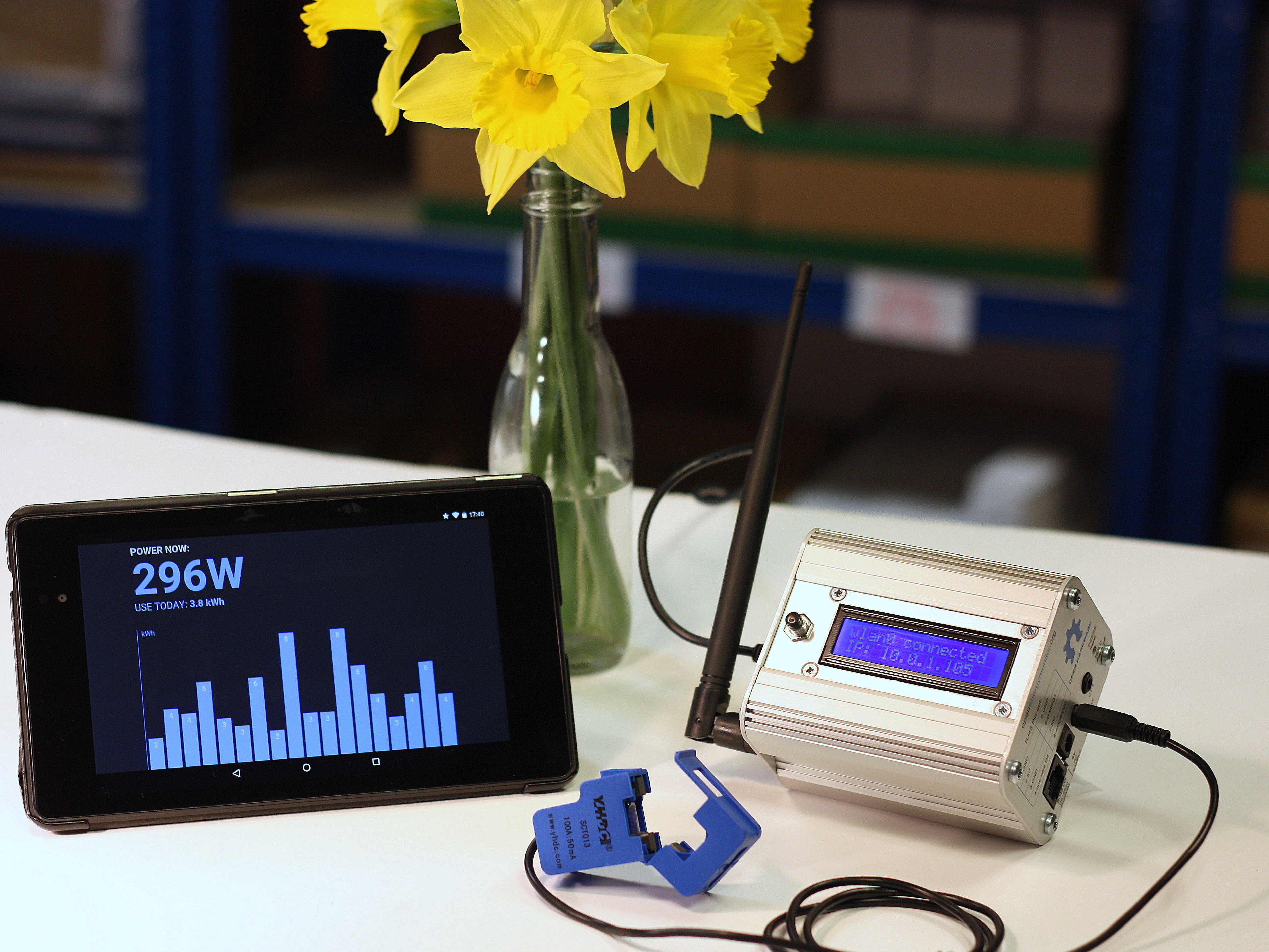
Hey there! In today’s hyper-connected world, remote IoT monitoring has become a game-changer for managing devices across industries. With SSH (Secure Shell) protocols, organizations can securely keep an eye on IoT devices from afar, ensuring peak performance and rock-solid security. In this article, we’re diving deep into remote IoT monitoring, exploring how SSH fits into the picture, and giving you a step-by-step guide to download and set up the tools you need to take control of your IoT ecosystem.
Let’s face it—technology is evolving at lightning speed, and the Internet of Things (IoT) has taken center stage in almost every part of our lives. Whether it’s smart homes, industrial automation, or even wearable tech, IoT devices are reshaping how we interact with the world. But managing these devices efficiently isn’t just about plugging them in and hoping for the best. You need robust solutions that can operate securely and effectively, even when you’re miles away from the actual devices.
This article is your ultimate guide to remote IoT monitoring using SSH. We’ll break down everything you need to know, from the basics to advanced tips, so you can enhance your IoT setup. Whether you're just starting out or you're a seasoned pro, this guide will help you understand why remote IoT monitoring matters and how SSH can be your secret weapon for secure communication between devices.
Read also:Nasa Astronauts Return To Earth After Historic Space Mission
What Exactly is Remote IoT Monitoring?
Breaking Down Remote IoT Monitoring
Remote IoT monitoring is like having a virtual set of eyes and hands that let you watch over and control IoT devices from anywhere in the world. This process allows administrators to collect real-time data, analyze performance metrics, and troubleshoot problems without ever needing to physically touch the devices. For businesses managing large-scale IoT setups—think smart cities, agricultural sensors, or industrial machinery—remote monitoring is a lifesaver.
Implementing remote IoT monitoring can bring a host of benefits to the table:
- Cost Savings: Minimize the need for on-site visits, cutting down on travel time and expenses.
- Reliability Boost: Proactively monitor and maintain systems to reduce downtime and keep everything running smoothly.
- Enhanced Security: Detect and address potential threats in real-time, safeguarding your data and infrastructure.
Why SSH is the Key to Secure Remote IoT Monitoring
SSH (Secure Shell) is like the superhero of network protocols, ensuring that communication between devices stays private and secure, even over unsecured networks. When it comes to remote IoT monitoring, SSH plays a critical role in keeping data safe. It encrypts the communication channels, making sure no unauthorized snoops can access sensitive information. Without SSH, your IoT devices could be vulnerable to cyberattacks, data breaches, and other nasty surprises.
Here’s why SSH is so important for remote IoT monitoring:
- Data Encryption: Keeps your data private during transmission, so prying eyes can't intercept it.
- Authentication: Verifies the identities of users and devices to prevent unauthorized access.
- Secure File Transfer: Allows you to update firmware or retrieve logs without compromising security.
Why Remote IoT Monitoring is a Must-Have
Supercharging Operational Efficiency
Remote IoT monitoring gives organizations the power to optimize their operations by providing real-time insights into how their devices and systems are performing. Imagine being able to keep tabs on multiple devices all at once, spotting issues early, and resolving them before they cause major problems. This level of visibility can significantly reduce downtime and boost overall efficiency. For example, in the agriculture industry, remote IoT monitoring can help farmers keep an eye on soil moisture levels, weather conditions, and crop health without having to physically visit their fields every day.
Fortifying Data Security
As IoT devices become more interconnected, the risk of cyberattacks increases. That’s where remote IoT monitoring with SSH comes in. It ensures that communication between devices stays secure, protecting sensitive data from unauthorized access. By implementing robust security measures, organizations can shield their IoT infrastructure from potential threats like data breaches, malware attacks, and unauthorized access.
Read also:The New York Giants A Legacy Of Football Greatness
Saving Money Where It Counts
One of the biggest advantages of remote IoT monitoring is the cost savings it offers. By eliminating the need for on-site visits, businesses can save time and resources while maintaining high levels of performance and security. Plus, remote monitoring allows for proactive maintenance, reducing the chances of costly repairs or replacements down the line.
How to Get Your Hands on Remote IoT Monitoring Tools
Picking the Right Tool for the Job
Choosing the right remote IoT monitoring tool is like finding the perfect pair of shoes—it has to fit your needs perfectly. When selecting a tool, consider factors like ease of use, scalability, and compatibility with your existing systems. Some popular options include:
- ThingsBoard
- Losant
- Freeboard
- Node-RED
Each tool brings something unique to the table, so it’s important to evaluate your specific requirements before making a decision. For instance, if you’re looking for a highly scalable solution, ThingsBoard might be the way to go. On the other hand, Freeboard could be a better fit for smaller projects.
Downloading and Installing Your Chosen Tool
Once you’ve picked the tool that suits your needs, the next step is to download and install it. Most remote IoT monitoring tools offer downloadable packages for various operating systems, including Windows, macOS, and Linux. Here’s a quick guide to get you started:
- Head over to the official website of the tool you’ve chosen.
- Find the download section and select the package that matches your operating system.
- Run the installer and follow the on-screen instructions to complete the setup process.
For tech-savvy users, many tools also offer installation via command-line interfaces or containerization platforms like Docker, giving you even more flexibility.
Setting Up Remote IoT Monitoring with SSH
Configuring SSH for Your IoT Devices
Before you can start monitoring IoT devices from afar, you’ll need to set up SSH on each device. This usually involves a few simple steps:
- Enable SSH on the device by diving into its settings menu or tweaking its configuration file.
- Generate SSH keys to ensure secure authentication between devices.
- Set up port forwarding if necessary, allowing remote access through firewalls or routers.
Keep in mind that SSH configurations can vary depending on the specific device and operating system you’re using. Always check the manufacturer’s documentation for detailed instructions.
Connecting to IoT Devices via SSH
With SSH configured on your IoT devices, you’re ready to connect to them remotely using an SSH client. Some popular options include:
- PuTTY (Windows)
- Terminal (macOS/Linux)
- SecureCRT
Connecting to an IoT device via SSH is a breeze. Here’s how you do it:
- Open your chosen SSH client and enter the device’s IP address or hostname.
- Specify the SSH port number (the default is 22).
- Authenticate using the SSH keys you generated or your password credentials.
Best Practices for Remote IoT Monitoring
Fortifying Security with Strong Measures
When it comes to remote IoT monitoring, security should always be at the top of your priority list. To keep your IoT infrastructure safe, follow these best practices:
- Strong Passwords: Use unique, complex passwords for all devices and accounts to deter hackers.
- Regular Updates: Keep your firmware and software up to date to patch any vulnerabilities.
- Network Segmentation: Isolate IoT devices from other systems to minimize the risk of cyberattacks.
Staying on Top of Device Performance
Regularly monitoring device performance is essential for keeping your systems running smoothly. By keeping an eye on key metrics like CPU usage, memory consumption, and network activity, administrators can quickly spot and fix potential issues before they spiral out of control. Many remote IoT monitoring tools come with built-in dashboards and alerts, making it easier to stay on top of things.
Maintaining Your IoT Infrastructure
To ensure your IoT setup remains reliable in the long run, it’s important to perform regular maintenance tasks. Here’s what you should focus on:
- Backup Configurations: Regularly back up your configuration files and data to prevent data loss.
- Test Failover Mechanisms: Make sure your disaster recovery plans are solid by testing them regularly.
- Review Logs: Keep an eye on logs for signs of suspicious activity or performance degradation.
Real-World Success Stories in Remote IoT Monitoring
How Different Industries Are Using Remote IoT Monitoring
Remote IoT monitoring has been making waves across various industries, proving its versatility and value. Here are a few examples:
- Healthcare: Real-time monitoring of patient vital signs and medical equipment to improve patient care.
- Manufacturing: Tracking machine performance to optimize production processes and reduce downtime.
- Energy: Managing smart grid systems and renewable energy sources to ensure efficient energy distribution.
These applications show just how powerful remote IoT monitoring can be in enhancing operational efficiency and security.
Stories from the Front Lines
Many organizations have seen incredible benefits from implementing remote IoT monitoring solutions. For instance, a major agricultural company cut water usage by 30% by using remote IoT sensors to monitor soil moisture levels. Similarly, a healthcare provider improved patient outcomes by implementing real-time monitoring of medical devices in remote locations.
What’s Next for Remote IoT Monitoring?
Trends Shaping the Future
As technology continues to advance, several exciting trends are set to shape the future of remote IoT monitoring:
- Artificial Intelligence & Machine Learning: Leveraging AI and ML for predictive analytics and anomaly detection to stay one step ahead of potential issues.
- Edge Computing: Processing data closer to the source to reduce latency and improve performance.
- 5G Networks: Enhancing connectivity and bandwidth to support larger and more complex IoT deployments.
Challenges on the Horizon
While the future looks bright, there are some challenges organizations may face:
- Data Privacy: As more devices become interconnected, protecting user data will be more important than ever.
- Scalability: As IoT deployments grow in size and complexity, ensuring systems can scale effectively will be crucial.
- Security Threats: Cyberattacks are becoming more sophisticated, so staying ahead of these threats will be key to maintaining secure IoT ecosystems.
Wrapping It Up
So there you have it—remote IoT monitoring with SSH is a powerful solution that can transform the way you manage and secure IoT devices across industries. By following the guidelines and best practices we’ve covered in this article, you can unlock the full potential of remote IoT monitoring to boost operational efficiency, enhance data security, and cut costs. We encourage you to download and implement remote IoT monitoring tools to experience these benefits firsthand.
Feel free to share your thoughts and experiences in the comments below. And don’t forget to check out other articles on our site for more insights into IoT technologies and applications. Together, let’s shape the future of connected systems!
Table of Contents
- Understanding Remote IoT Monitoring
- Why Remote IoT Monitoring Matters
- How to Download Remote IoT Monitoring Tools